CISSP Certification Prep iOS and Android App
Ace your CISSP exam with CISSP Certification Prep!
Our app is designed to give you an immersive, realistic test-prep experience.
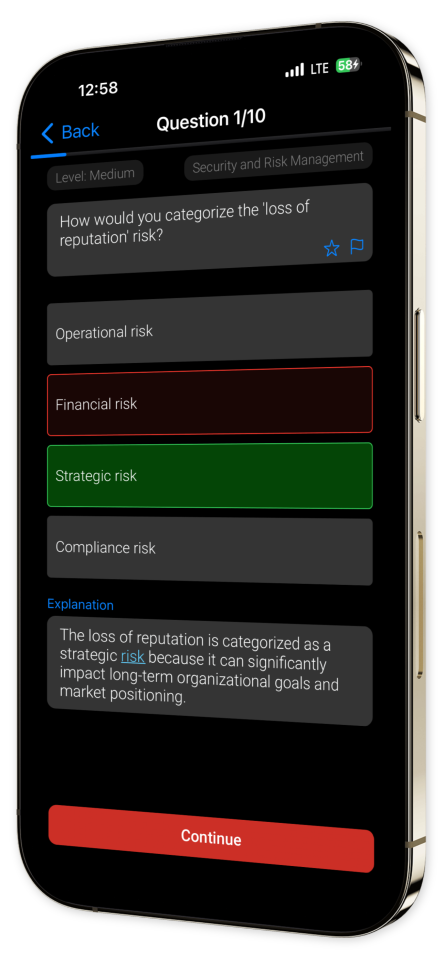
Dive into an expansive question bank covering all eight CISSP domains to elevate your cybersecurity knowledge and skills. Each question includes detailed explanations to deepen understanding and sharpen your strategy.
Key Features:
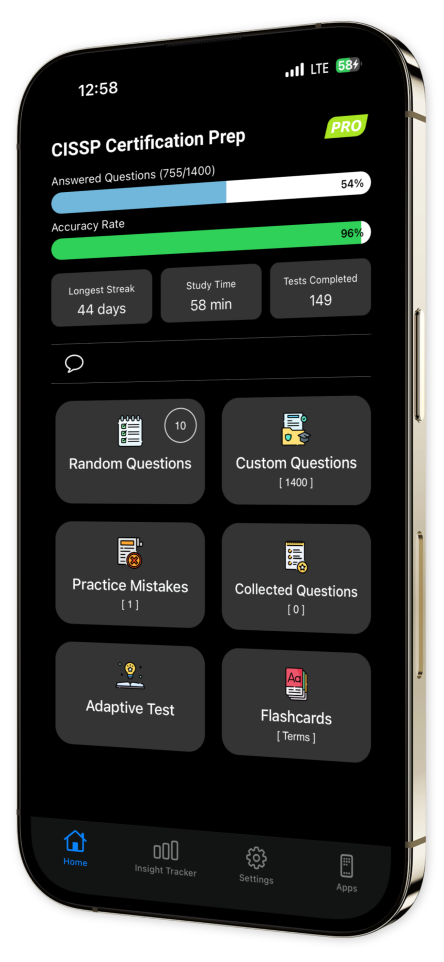
Extensive Question Bank: Practice across all essential topics for comprehensive coverage and robust preparation.
In-Depth Explanations: Get insightful answers with thorough rationales to boost learning and retention.
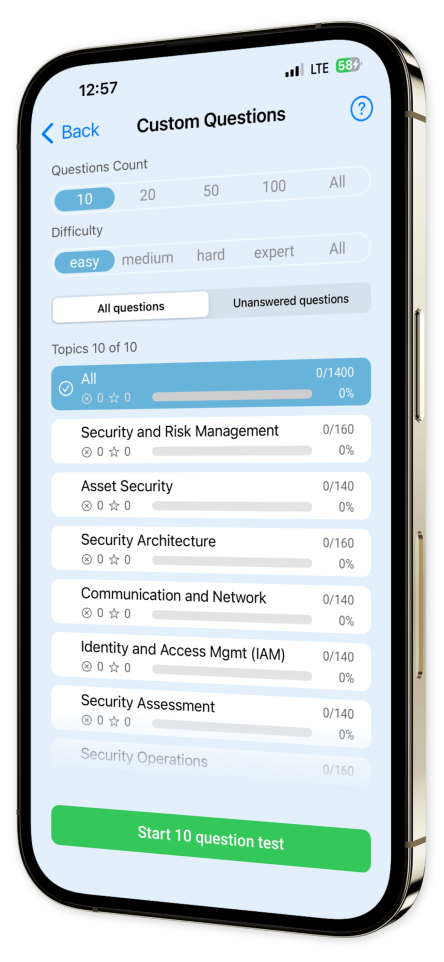
Custom Test Creation: Build personalized quizzes by selecting domains and question types to target your weak areas.
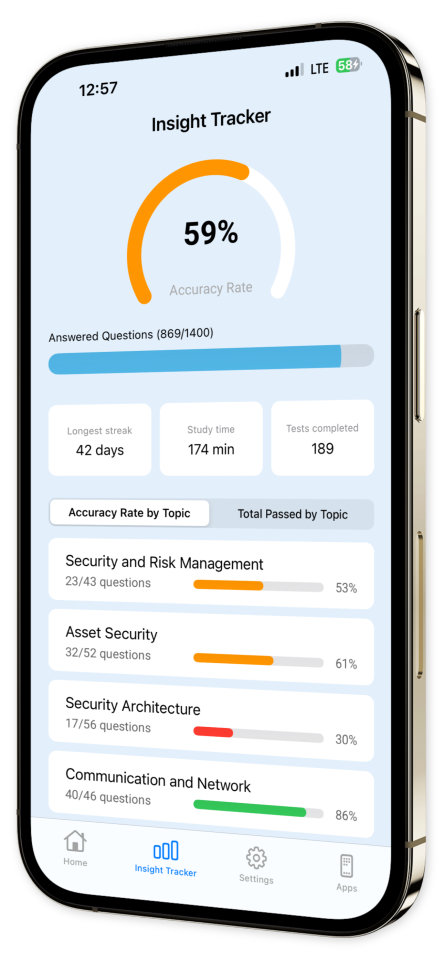
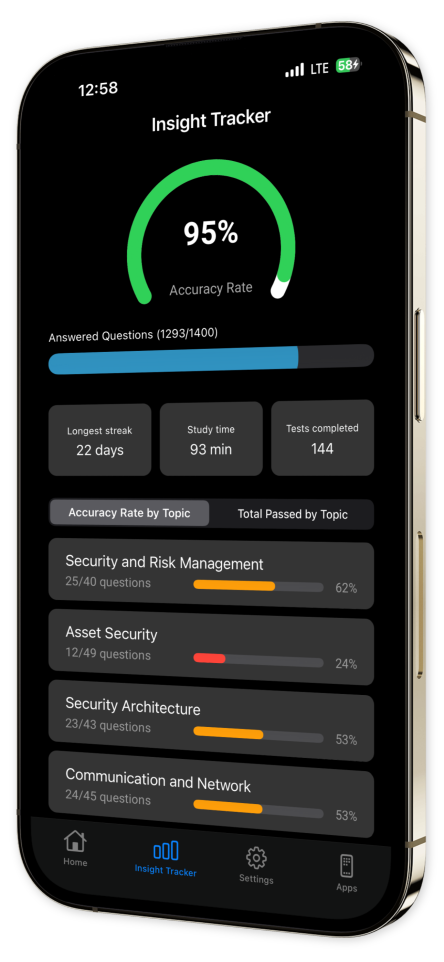
Progress Tracking: Monitor improvement over time with intuitive tracking to evaluate your mastery.
Offline Access: Study anytime, anywhere—even without internet—perfect for on-the-go learning.
User-Friendly Interface: An organized, intuitive design that keeps your focus on mastering cybersecurity content.
Download CISSP Certification Prep today and start a smarter, more effective path to your Certified Information Systems Security Professional credential.
Empower your career with the credentials you deserve.
Simplify your preparation journey.
Seize the opportunity to grow your cybersecurity expertise—get started now!
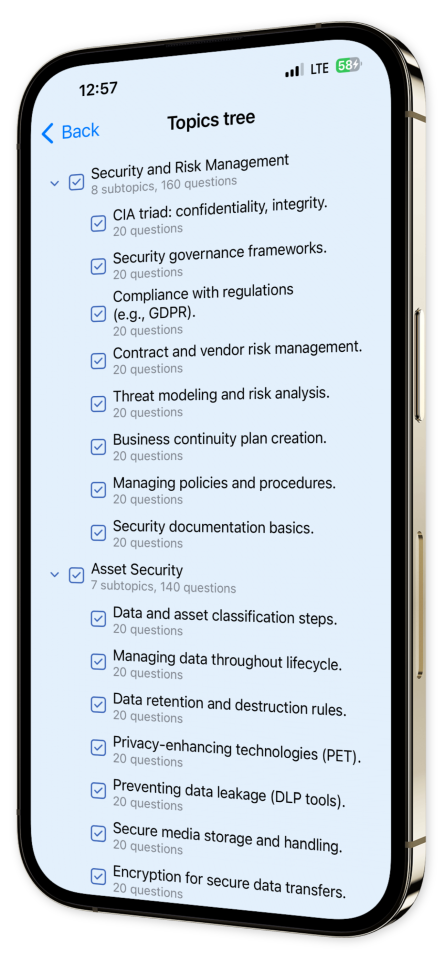
Content Overview
Explore a variety of topics covered in the app.
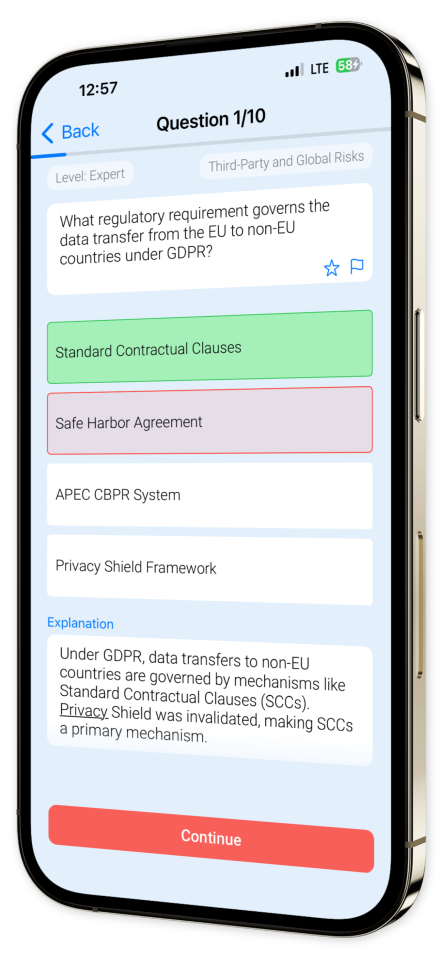
Example questions
Let's look at some sample questions
An IT system's data is duplicated to a site to ensure access in disasters. Which CIA triad component is this?
AvailabilityIntegrityConfidentialityAuthenticity
Duplicating data to a remote site ensures availability by providing access to data during disasters, fulfilling availability requirements.
An organization restricts employee access to sensitive files. Which CIA triad principle is being followed?
ConfidentialityAvailabilityIntegrityAccessibility
Restricting access to sensitive files ensures confidentiality, preventing unauthorized access to sensitive information.
Company A, based in the US, collects data from EU citizens. What is the primary regulation that dictates data protection standards in this scenario?
CLOUD ActPDPAGDPRHIPAA
The GDPR (General Data Protection Regulation) applies to organizations that process personal data of EU citizens, regardless of the company's location.
An EU company transfers data to a non-EU partner. Which compliance method aligns with GDPR's Article 46?
Binding Corporate RulesPrivacy ShieldSafe HarborEU-U.S. Privacy Shield
Binding Corporate Rules are a mechanism under GDPR's Article 46 that allow data transfers to non-EU countries ensuring protection.
What factor is most critical when selecting a vendor?
Employee countGeographic locationCompliance with regulationsSocial media presence
Compliance with regulations is critical to ensure that the vendor meets legal and industry standards.
Which tool is primarily used to manage vendor contracts and associated risks?
Risk RegisterVendor Management SystemIncident Response PlanData Warehouse
A Vendor Management System is used to manage vendor contracts, performance, and associated risks.
During BCP creation, what is the first step in the business impact analysis process?
Identify critical business functionsDevelop recovery strategiesConduct a risk assessmentTest the business continuity plan
The first step in a business impact analysis is to identify and prioritize critical business functions because this step sets the foundation for understanding the impact of disruptions.
What should be prioritized first in a BCP risk assessment?
Critical business functionsCost of recoveryPotential downtimeEmployee safety
In any emergency plan, human life and safety are the top priorities, overriding all other considerations including business functions.
Before retiring an outdated policy, what step is essential?
Delete all copies of the policyInform all staff of its retirementReview its effectiveness historicallyHire a consultant for advice
Reviewing the historical effectiveness of a policy ensures that lessons learned inform future policy creation and maintenance.
Identify the key factor in determining policy effectiveness in a global organization?
Policy lengthEmployee feedbackCultural adaptabilityManagement enforcement
Cultural adaptability is critical in a global organization, ensuring policies are effectively implemented across different regions with varying cultural norms.